What is a VPN?
The term virtual private network (abbreviated VPN) describes any technology that can encapsulate and transmit network data, typically Internet Protocol data, over another network. Such a system enables users to access network resources that may otherwise be inaccessible from the public internet. VPNs are frequently used in the information technology sector to provide access to resources for users that are not physically connected to an organization’s network, such as telecommuting workers. VPNs are so named because they may be used to provide virtual (as opposed to physical) access to a private network. – Wikipedia.
This was the original use for a VPN, office to office encrypted traffic.
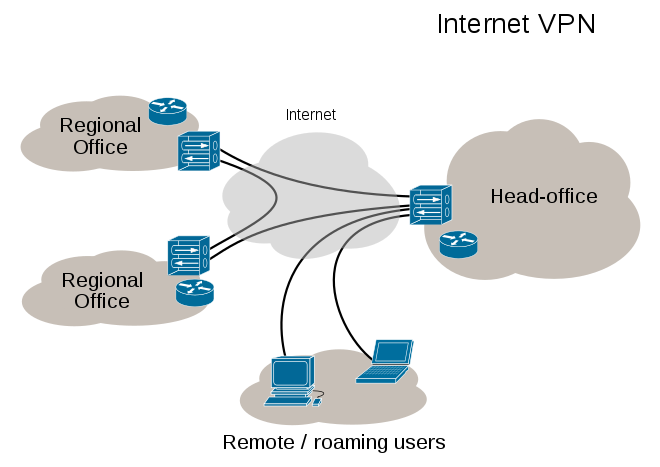
This is how VPNs are marketed to us today.
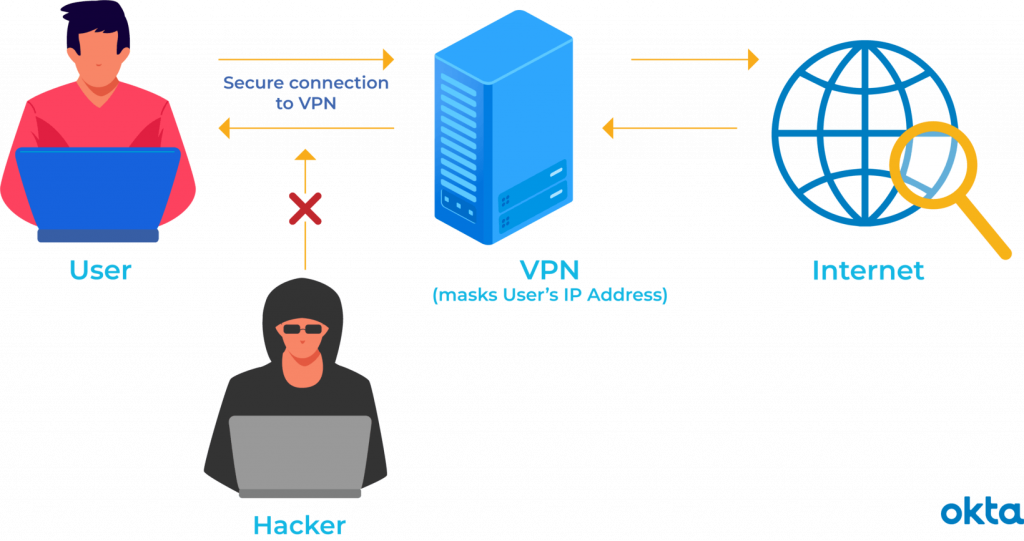
This is the reality of what the marketing really is.
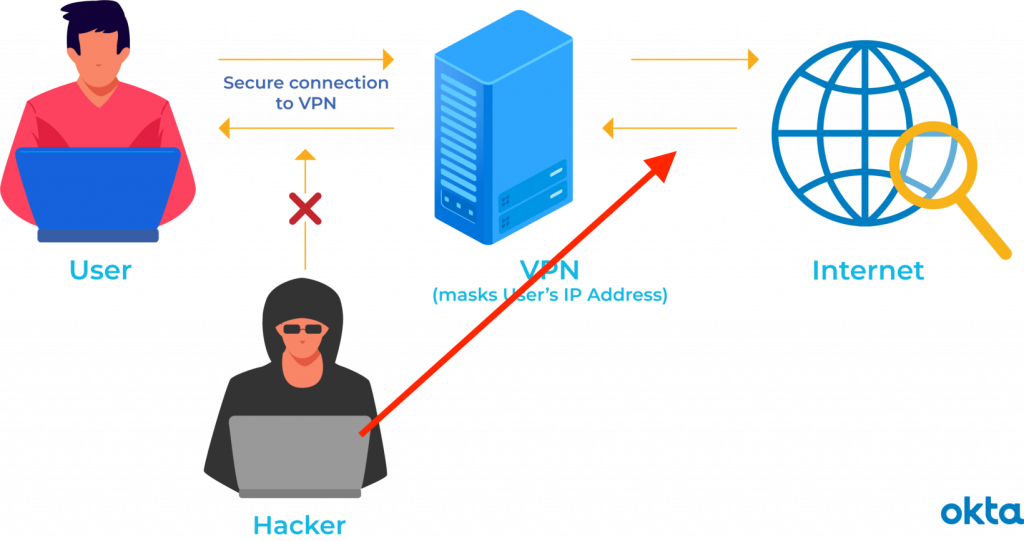
A VPN makes it appear you are connecting from a different part of the world then you might actually be connecting from.
What Will Your VPN Hide & From Whom?
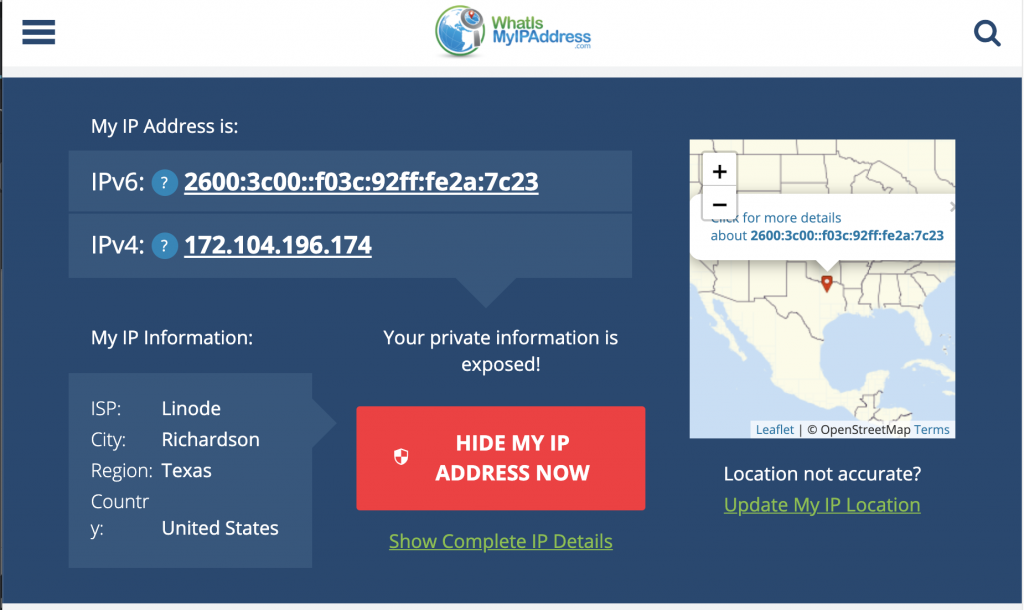
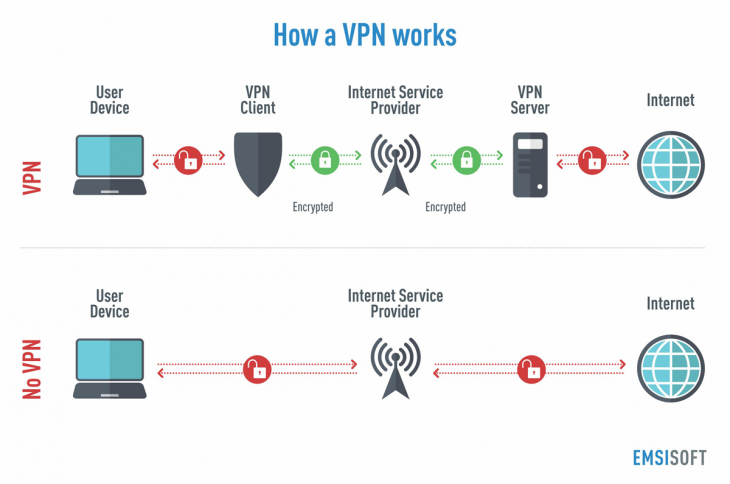
Ordinarily, when you go online, your internet service provider (ISP) provides your connection. It keeps track of you via an IP address. Your web traffic passes through your ISP’s servers — they can log and see everything you do online. They handle your DNS requests, thus they know where you are visiting.
Your local ISP may seem trustworthy, but they could be handing your browsing history over to advertisers, the police or government, and other third-parties. Your ISP is also open to breaches: if they get hacked, your personal and private data could be compromised.
It has also been reported by arstechnica.com – “All major ISPs denied selling or sharing their users’ browsing histories and other sensitive information in 2017, when they convinced Congress and President Trump to prevent implementation of broadband privacy rules. But since then, it has been reported that T-Mobile, Sprint, and AT&T were selling their mobile customers’ location information to third-party data brokers despite promising not to do so.”
This is especially worth considering if you regularly connect to public Wi-Fi networks. You never know who could be watching your internet traffic from the other side and potentially stealing from you — passwords, personal data, payment information, and even your identity.
Present-day use of VPNs
According to GlobalWebIndex, Between 2016 and 2018, the number of VPN users worldwide increased by over four times. In countries like Thailand, Indonesia, and China, where internet usage is restricted and censored, as many as one in five internet users utilize a VPN.
Meanwhile, in the USA, UK, and Germany, the percentage of VPN users is lower but not insignificant, at around 5%.
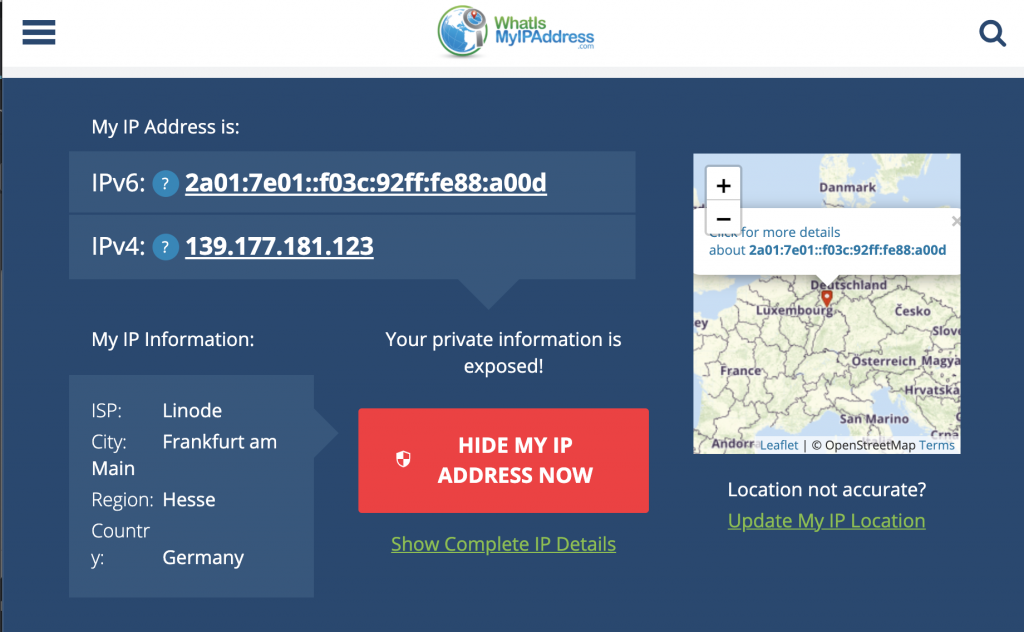
One of the biggest drivers for VPN uptake in recent years has been the increasing demand for users to access geo-restricted content. For instance, video streaming services like Netflix, Hulu, and YouTube make specific videos only available in certain countries. Modern VPNs allow you to encrypt your IP so that it seems you are browsing from another country, allowing users to access this content from anywhere.
When should you really use a VPN?
- When you want to keep some control over your privacy. The VPN will hide your real IP address from websites you visit and peer-to-peer nodes you connect to. It also prevents ISPs and mobile network operators from tracking the domains and IPs you visit.
Protecting your connection from ‘Man in the Middle’ and other common attacks on networks you don’t trust. Useful when connected to Wi-Fi in airports, hotels, cafes and libraries. Please see these posting for why #2 was removed.- Circumventing censorship or geographical blocks on websites and content. Some VPNs can help you retrieve information, media & crypto exchanges that otherwise might be inaccessible.
But remember this about a VPN
When you log into an account like Netflix, Amazon, Fakebook FaceBook, Twitter, etc. they already have your personal information. All these types of accounts have your email address, home address, real name, credit card or bank account. Hiding your IP address does nothing to protect your identity.
Tracking like Google Analytics and MetaPixel know who you are even when you log out of sites listed above.
Remember that if you use a commercial VPN, your internet traffic goes through the VPN provider’s network. Whoever is in control of the servers can see and log anything you do online, if they choose to. You better trust the service you are signing up for – we will get to that in a future post of VPN Worst Practices.
How do they know you are coming from a VPN?
0:11
In this video today, I’m going to show you how easy it is to identify a connection coming in from a VPN. But I’m going to break it down into two types of VPNs. This time? This little descriptor, this little image shows you how a VPN was originally a VPN was between two offices. So they needed a virtual private network between the two, you know, like maybe the head office and a regional office. And so they needed all that data encrypted between the two, and that’s how a VPN originally was functioning.
0:56
And in today’s environment, it’s more of a consumer, the consumer sold product that doesn’t necessarily do what you want it or you think it’s going to do, and that was kind of in a prior video. But we’re not going to go over office to office VPN connections.
1:20
We’re going to do more of using this diagram of how a VPN works, where it’s between your computer and the Internet instead of your computer and the, the home office.
1:35
And the reason why it’s really easy to find what a connection is for a VPN.
1:43
And that’s really based on what they’ll call a an Erin Number.
1:50
Or, Erin has this list. And it’s an a S N number.
1:59
And an ASN number is issued to a block of IP addresses. And that is how an IP address is identified on who the owner is. And that’s important, because that will tell you what type of traffic it is.
2:18
For example, if you go to Comcast and look up their ASN numbers, you’ll see that, you know, they have 71 million IP V four and they have just more IPV six is than you could ever possibly use. And they’re mainly in the United States, and I think that’s really all they are.
2:41
And so when you look up their ASN number, you know that Comcast, cable, users, their IP addresses for home users and business users. So you know what type of usage it is.
2:56
Comcast Port, this set of IP addresses, doesn’t have any data center usage, meaning a server that’s located at a data center. Comcast uses these IP addresses for commercial and residential connections.
3:13
So they know, well, the, the, the service providers, the data providers, know that this AS M A S N number, is a good one to allow what I’ll call real IP addresses. Through and a real IP address, what I consider a real IP address.
3:32
Is an end user at home in a coffee shop At work.
3:39
And so you know that there’s a real person behind that IP address as compared to someone like GoDaddy and GoDaddy, they have IP addresses that mainly sit in a server, in a server farm, in a colo where all a bunch of servers are because you don’t subscribe to GoDaddy as a service provider.
4:06
GoDaddy does not make a connection into your home, but GoDaddy has a bunch of servers located, you know, around the US.
4:16
It looks like mainly Scottsdale.
4:19
And they will, you know, if you have a website hosted at GoDaddy it’s not your connection from they are servers out to the internet.
4:30
Their servers are where your, your web page lives. So that IP adress really lives in a server farm and a co-location where there’s just a bunch of servers.
4:44
So that IP address range or that ASN number is not a real IP address where there’s a real human sitting at that IP.
4:54
And the same goes for my provider that I used for IP addresses for the VPN that I have.
5:03
It is behind servers, and that’s how easy it is to identify.
5:10
is it a real IP address where someone is sitting at their computer, or is it at a server farm, or a co-location, or something like that, where there’s not a real person behind that IP address.
5:24
And when you find out that the ASN number is just two a bunch of servers, you can easily block those IP addresses.
5:35
So, when you have something like this, which, this is a plugin, four that I use on our website, and this plugin is free.
5:49
I can enable it, and I can restrict someone coming in as an VPN connection, as a proxy.
5:59
And that’s how I easily block things and connections.
6:05
When someone is coming in from a proxy, potentially toure or a VPN connection, go right through here and show you that, you know, I can kind of graph it And see what type of connections are coming in.
6:23
This is when I re enabled it stronger, because we had some, some issues earlier. And people were coming in with a VPN, and then they found out that they couldn’t use a VPN, so that kind of dropped off.
6:37
But this is one way that any web site could easily implement and start blocking all VPN connections.
6:45
And it’s happening more and more.
6:48
When you visit websites, they want to know who is truly visiting their website.
6:54
And not just allowing VPN connections that are coming from, you know, random places that they, they honestly know that you’re coming in from a VPN, and if there were crypto exchanges that wanted to block those, some do, they can implement that tomorrow. So that’s something that, you know, everybody should be aware of.
7:15
if is, if you are relying on a VPN to connect to a and exchange that, that you connect to regularly, That could change in an instant. And so that’s one reason why we don’t recommend keeping your coins on an exchange, because you don’t know what’s going to happen tomorrow, all of a sudden, a decision could be made.
7:37
And because you’re representing yourself that you are coming from a particular country, but you’re not coming from that country.
7:45
If they decide to flip that switch, well, you know, they warned you don’t come in with a VPN connection, Represent where you’re coming from, with a connection that you’re coming from.
7:55
And if they decide to turn that switch on, then you’re going to have to figure out how to get those coins off. If there are coins left on there. So, it is really easy to see that someone’s using a VPN.
8:09
And I just kinda wanted to show you some of the tricks and tips, and this is just a browser plugin, sorry, not a browser plugin, AM, a plugin that we use to block VPN Connections.